Autorun: Difference between revisions
No edit summary |
No edit summary |
||
| (9 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
Disambiguation "autorun" in this context refers to a feature or property of Microsoft Windows and other operating systems, in general, that exhibit the behavior of automatically executing software on an inserted cdrom or media. | Disambiguation "autorun" in this context refers to a feature or property of Microsoft Windows and other operating systems, in general, that exhibit the behavior of automatically executing software on an inserted cdrom or media. | ||
Some terminology relating to or sometimes used synonymously are '''Autoplay''', ''' | Some terminology relating to or sometimes used synonymously are '''Autoplay''', '''Autorun''', and '''Auto-insert notification'''. Some sources use the terms autorun and autoplay interchangeably, while others point out that Autoplay is an enhancement to autorun introduced in Windows XP, where as autorun itself dates back to Windows 95. Autoplay will distinguish different media types and content types taking different preprogrammed action for each type. For example, a music CD will take a different action from a data CD being inserted. | ||
Whenever inserting DVD's or CD's into a Windows computer you are usually prompted with a message asking what to do with the disc. This happens because of the AutoPlay/Auto Insert Notification functionality built into Windows. This can cause problems when burning discs using DVD/CD duplicators. | Whenever inserting DVD's or CD's into a Windows computer you are usually prompted with a message asking what to do with the disc. This happens because of the AutoPlay/Auto Insert Notification functionality built into Windows. This can cause problems when burning discs using DVD/CD duplicators. | ||
| Line 7: | Line 7: | ||
There are security implications involved with this behavior, such as the well known [[Sandisk U3 Flash Drive Virus]] and the more notorious [[Sony DRM Rootkit]]. | There are security implications involved with this behavior, such as the well known [[Sandisk U3 Flash Drive Virus]] and the more notorious [[Sony DRM Rootkit]]. | ||
The autorun behavior can launch software without your consent and furthermore, actually install malware on your computer without your knowledge with full stealth proficiency. | The autorun behavior can launch software without your consent and furthermore, actually install malware on your computer without your knowledge with full stealth proficiency. | ||
<big>Note: This article describes more than one method to disable this behavior. The best recommended method is to use '''Group Policy Editor'''. For the impatient, simply read [[#Turn off Autoplay With Group Policy Editor]] or look for it in this guide below.</big> | |||
== Security == | |||
Windows worms including Stuxnet and Conficker were able to spread onto networks after unwitting victims plugged infected USB sticks into PCs. This has happened automatically in cases where autorun was enabled, as it did in default on older versions of Windows until a change pushed by Microsoft. | |||
Note that in recent Linux distributions autorun is typically disabled for security reasons. You will find that it has even been disabled in Windows since XP service pack 2. | |||
In regards to Linux autorun security implications, one known exploit took advantage of a now patched flaw in GNOME Evince document viewer. The exploit made it possible to insert a USB stick with modified code into an Ubuntu PC to get rid of a screensaver without entering a password and display the user’s desktop. | |||
Clarification - On both Windows and Linux currently, post autorun vulnerability awareness these OS behave in a way as not to automatically execute a program, but still poll the drive and prompt the user for action. Disabling autorun is not the same as disabling drive polling, the second being a deeper level modification. | |||
== | == Temporarily Disable Auto Insert Notification and Autorun Behavior == | ||
Hold down the <big>'''SHIFT KEY'''</big> when inserting a thumbdrive, cdrom disc, or other related media to prevent autorun.inf from launching. You can temporarily disable the AutoPlay feature in Windows 2000, XP, 2003 by holding down the left Shift key as the CD begins to run. In addition if you wish to browse the contents of the CD open My Computer, right-click the CD-ROM drive and choose explore. | |||
== Turn off Autoplay With Group Policy Editor == | |||
{{:Turn off Autoplay With Group Policy Editor}} | |||
=== Policy Edit in the Windows Registry === | |||
This is low level approach to manipulating policies in Windows. If you use Group Policy Editor you will '''NOT''' need to do this. | |||
Open 'regedit' and locate the key: | Open 'regedit' and locate the key: | ||
| Line 45: | Line 45: | ||
#enter "95 00 00 00" as the value | #enter "95 00 00 00" as the value | ||
Update: The default settings for NoDriveTypeAutorun are different between Windows 2000/2003 and Windows XP/Vista. This is explained very well by Minkus on edugeek.net in the thread [http://www.edugeek.net/forums/windows/25714-advanced-autorun-autoplay-settings-adm-file.html Advanced Autorun / Autoplay settings ADM file] (''mirrored on our talk page''). Credit to Minkus. | |||
== Other Ways to Disable Behavior == | |||
=== soft disable === | |||
Windows | Disabling AutoPlay in Windows XP through Windows Explorer | ||
#Open My Computer or Explorer | |||
#Right-click the CD-ROM drive or other drive and click Properties. | |||
#Click the AutoPlay tab. Within this section you will be able to specify all Windows AutoPlay features. | |||
# | Disable AutoPlay on audio CDs | ||
# | #Click Start, Programs, Windows Explorer | ||
# | #Within Explorer click View and then Folder Options. | ||
# | #Click the File Types tab and locate "CD Audio Track" category within the list of available file types. | ||
# | #Highlight " CD Audio Track" and click Edit or Advanced. | ||
#In the Actions category change the default from Play to Open or none. | |||
Windows | The Windows Registry solution below is the most effective, in that it prevents any drive io activity after media is inserted, however, also has some technical ramifications. | ||
=== Stop Drive Polling === | === Stop Drive Polling === | ||
| Line 83: | Line 78: | ||
<big>Remember (''or allow me to clarify'') that there are two different processes involved. One is '''polling''' which is to see if a disk has been inserted. That's what allows Windows to know there's a disk or media present in the first place. Autoplay is a subsidiary process in that it controls whether Windows attempts to run a found disk. </big> | <big>Remember (''or allow me to clarify'') that there are two different processes involved. One is '''polling''' which is to see if a disk has been inserted. That's what allows Windows to know there's a disk or media present in the first place. Autoplay is a subsidiary process in that it controls whether Windows attempts to run a found disk. </big> | ||
=== Additional Security and Support === | |||
CERT ADVISORY 14 Apr 2009: VU#889747: [https://www.kb.cert.org/vuls/id/889747 Microsoft Windows fails to properly handle the NoDriveTypeAutoRun registry value]. This issue is addressed for Windows Vista and Server 2008 systems in Microsoft Security Bulletin [http://www.microsoft.com/technet/security/bulletin/ms08-038.mspx MS08-038]. This update corrects the behavior of NoDriveTypeAutoRun on those platforms. Windows 2000, XP, and Server 2003 users should install the update in Microsoft Support Document [http://support.microsoft.com/kb/967715 KB967715]. | |||
From that advisory: With limited testing, it appears to be possible to disable AutoRun and AutoPlay on Microsoft Windows systems by saving the following text as a .REG file and importing it into the registry: | |||
REGEDIT4 | |||
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf] | |||
@="@SYS:DoesNotExist" | |||
This registry value appears to prevent windows from parsing and taking actions based on the Autorun.inf file, which both AutoRun and AutoPlay utilize. Note that Windows can cache AutoRun capabilities of devices via the MountPoints2 registry key, though. So even after disabling AutoRun as described above, Windows may still automatically execute files on devices that Windows has listed in this cache. For this reason, we also recommend removing this cache by deleting the MountPoints2 registry key for each user: | |||
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2 | |||
== Make Your Own User Created CDROM, DVD and USB Media Autorun == | == Make Your Own User Created CDROM, DVD and USB Media Autorun == | ||
| Line 94: | Line 103: | ||
See [[Creating an Autorun.inf]] for more information. | See [[Creating an Autorun.inf]] for more information. | ||
== Linux Specific == | |||
In Linux autorun automagically recognises all available CDROMs in your system, mounts them upon insertion and executes a possible 'autorun' executable on the CD. To allow an ordinary user to do this you have to add the options user,exec in /etc/fstab to the CDROMs you want to use. | |||
There is also Autorun.desktop for KDE. | |||
== References and Sources == | == References and Sources == | ||
| Line 101: | Line 116: | ||
* Moon Valley Software [http://autorun.moonvalley.com/autoruninf.htm Autorun.inf, What is it?] | * Moon Valley Software [http://autorun.moonvalley.com/autoruninf.htm Autorun.inf, What is it?] | ||
== Related == | |||
* [[Autorun|Autoplay, Autorun, and Auto-insert notification]] | |||
* [[Turn off Autoplay With Group Policy Editor]] | |||
* [[Sandisk U3 Flash Drive Virus]] | |||
* [[Sony DRM Rootkit]] | |||
For Linux Users: | |||
* [[How_Do_I:_A_Linux_Q%26A#.5BDISABLE_ANNOYING_KDE_Autorun_WHEN_CDROM_IS_IN_DRIVE_WHEN_KDE_STARTS.5D|KDE Autorun]] | |||
| | ||
| Line 111: | Line 133: | ||
[[Category:Microsoft]] | [[Category:Microsoft]] | ||
[[Category:Windows]] | [[Category:Windows]] | ||
[[Category:Linux]] | |||
[[Category:Software]] | [[Category:Software]] | ||
[[Category:Security]] | [[Category:Security]] | ||
Latest revision as of 11:43, 31 March 2016
Disambiguation "autorun" in this context refers to a feature or property of Microsoft Windows and other operating systems, in general, that exhibit the behavior of automatically executing software on an inserted cdrom or media.
Some terminology relating to or sometimes used synonymously are Autoplay, Autorun, and Auto-insert notification. Some sources use the terms autorun and autoplay interchangeably, while others point out that Autoplay is an enhancement to autorun introduced in Windows XP, where as autorun itself dates back to Windows 95. Autoplay will distinguish different media types and content types taking different preprogrammed action for each type. For example, a music CD will take a different action from a data CD being inserted.
Whenever inserting DVD's or CD's into a Windows computer you are usually prompted with a message asking what to do with the disc. This happens because of the AutoPlay/Auto Insert Notification functionality built into Windows. This can cause problems when burning discs using DVD/CD duplicators.
There are security implications involved with this behavior, such as the well known Sandisk U3 Flash Drive Virus and the more notorious Sony DRM Rootkit.
The autorun behavior can launch software without your consent and furthermore, actually install malware on your computer without your knowledge with full stealth proficiency.
Note: This article describes more than one method to disable this behavior. The best recommended method is to use Group Policy Editor. For the impatient, simply read #Turn off Autoplay With Group Policy Editor or look for it in this guide below.
Security
Windows worms including Stuxnet and Conficker were able to spread onto networks after unwitting victims plugged infected USB sticks into PCs. This has happened automatically in cases where autorun was enabled, as it did in default on older versions of Windows until a change pushed by Microsoft.
Note that in recent Linux distributions autorun is typically disabled for security reasons. You will find that it has even been disabled in Windows since XP service pack 2.
In regards to Linux autorun security implications, one known exploit took advantage of a now patched flaw in GNOME Evince document viewer. The exploit made it possible to insert a USB stick with modified code into an Ubuntu PC to get rid of a screensaver without entering a password and display the user’s desktop.
Clarification - On both Windows and Linux currently, post autorun vulnerability awareness these OS behave in a way as not to automatically execute a program, but still poll the drive and prompt the user for action. Disabling autorun is not the same as disabling drive polling, the second being a deeper level modification.
Temporarily Disable Auto Insert Notification and Autorun Behavior
Hold down the SHIFT KEY when inserting a thumbdrive, cdrom disc, or other related media to prevent autorun.inf from launching. You can temporarily disable the AutoPlay feature in Windows 2000, XP, 2003 by holding down the left Shift key as the CD begins to run. In addition if you wish to browse the contents of the CD open My Computer, right-click the CD-ROM drive and choose explore.
Turn off Autoplay With Group Policy Editor
Microsoft Windows Autorun can very effectively be disabled using the Windows Group Policy Editor. In Microsoft Windows, you use Group Policy to define user and computer configurations. It is a way to customize the behavior of the Windows operating system. There are advantages to disabling (Autoplay, Autorun, and Auto-insert notification) with Group Policy Editor as opposed to alternative methods. They include:
- Can be made to apply to all media, or just a CD drive
- Does not disable drive "polling," so the system will still know when media has been inserted/connected
- No direct registry editing with Registry Editor
- Prevents malware from automatically loading from media
OS Specific Methods Using Policy Editor
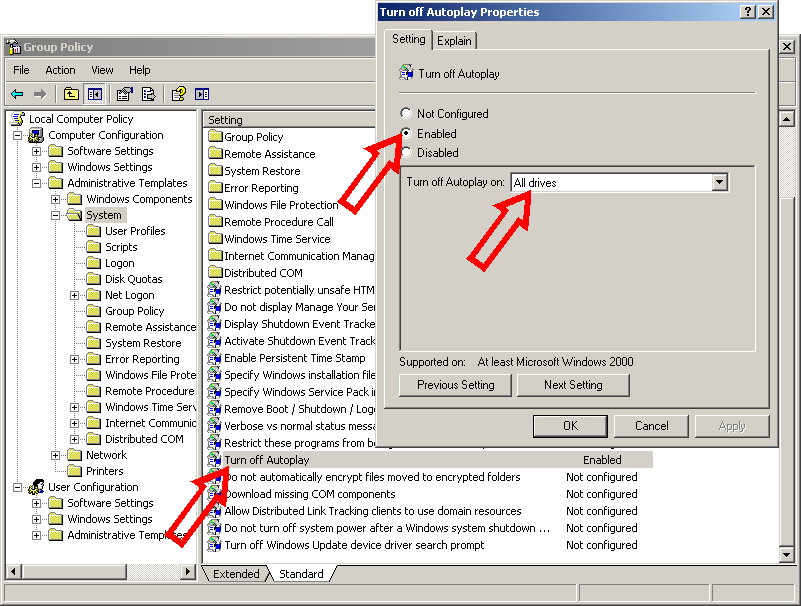
Windows XP Pro
- Remove media from the computer.
- Go to Start<Run, type 'gpedit.msc' (without the quotes) and click OK. This will open up the Group Policy Editor.
- Expand the following (in order): Computer Configuration<Administrative Templates<System.
- Click on the System folder, then on the right double-click on the 'Turn AutoPlay off' option.
- Select Enable and for 'Turn off AutoPlay on' set to All Drives. Click OK, close the Group Policy Editor and restart the computer.
The following illustration shows the Group Policy Editor in Windows XP
Windows Vista
- Remove media from the computer.
- Go to Control Panel<Hardware and Sound<Play CD's or other media automatically.
- Uncheck the box at the top of the window next to "Use AutoPlay for all media and devices".
- Click the Save button and close Control Panel.
- Optional: Same method for disabling in Windows XP Pro can also be used.
Windows 7
- Remove media from the computer.
- Go to Control Panel<Hardware and Sound<AutoPlay.
- Uncheck the box at the top of the window next to "Use AutoPlay for all devices".
- Click the Save button and close Control Panel.
Policy Edit in the Windows Registry
This is low level approach to manipulating policies in Windows. If you use Group Policy Editor you will NOT need to do this.
Open 'regedit' and locate the key:
HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
double-click the entry: "NoDriveTypeAutoRun" if present and change the value to
"95 00 00 00"
If NoDriveTypeAutoRun is not present, follow the below steps:
- click Edit from the drop down menu
- click new
- click binary value
- enter "NoDriveTypeAutoRun" as the name
- enter "95 00 00 00" as the value
Update: The default settings for NoDriveTypeAutorun are different between Windows 2000/2003 and Windows XP/Vista. This is explained very well by Minkus on edugeek.net in the thread Advanced Autorun / Autoplay settings ADM file (mirrored on our talk page). Credit to Minkus.
Other Ways to Disable Behavior
soft disable
Disabling AutoPlay in Windows XP through Windows Explorer
- Open My Computer or Explorer
- Right-click the CD-ROM drive or other drive and click Properties.
- Click the AutoPlay tab. Within this section you will be able to specify all Windows AutoPlay features.
Disable AutoPlay on audio CDs
- Click Start, Programs, Windows Explorer
- Within Explorer click View and then Folder Options.
- Click the File Types tab and locate "CD Audio Track" category within the list of available file types.
- Highlight " CD Audio Track" and click Edit or Advanced.
- In the Actions category change the default from Play to Open or none.
The Windows Registry solution below is the most effective, in that it prevents any drive io activity after media is inserted, however, also has some technical ramifications.
Stop Drive Polling
This is the most aggressive and most effective approach. The registry keys editor before dealt with Windows Policy a security feature of windows. Now will show the direct disable in the registry keys controlling the io specifically.
Windows 2000/XP
- Run the Registry Editor regedit and type that program name into the box after choosing "Run" from the Start menu.
- Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Cdrom.
- Double-click the Autorun value, and type 0 for its value. (If it's not there, create it by selecting Edit -> New -> DWORD Value, and typing "Autorun" for its name.)
- Log out and then log back in for this change to take effect.
SIDE EFFECT - With this solution, Windows will no longer be notified when you insert a new CD. To make sure the correct icon and title for the current CD are displayed in My Computer and Explorer, press F5 to refresh the window.
Remember (or allow me to clarify) that there are two different processes involved. One is polling which is to see if a disk has been inserted. That's what allows Windows to know there's a disk or media present in the first place. Autoplay is a subsidiary process in that it controls whether Windows attempts to run a found disk.
Additional Security and Support
CERT ADVISORY 14 Apr 2009: VU#889747: Microsoft Windows fails to properly handle the NoDriveTypeAutoRun registry value. This issue is addressed for Windows Vista and Server 2008 systems in Microsoft Security Bulletin MS08-038. This update corrects the behavior of NoDriveTypeAutoRun on those platforms. Windows 2000, XP, and Server 2003 users should install the update in Microsoft Support Document KB967715.
From that advisory: With limited testing, it appears to be possible to disable AutoRun and AutoPlay on Microsoft Windows systems by saving the following text as a .REG file and importing it into the registry:
REGEDIT4 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf] @="@SYS:DoesNotExist"
This registry value appears to prevent windows from parsing and taking actions based on the Autorun.inf file, which both AutoRun and AutoPlay utilize. Note that Windows can cache AutoRun capabilities of devices via the MountPoints2 registry key, though. So even after disabling AutoRun as described above, Windows may still automatically execute files on devices that Windows has listed in this cache. For this reason, we also recommend removing this cache by deleting the MountPoints2 registry key for each user:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2
Make Your Own User Created CDROM, DVD and USB Media Autorun
Autorun.inf is the primary instruction file associated with the Autorun and is a simple text configuration file. In Windows something called the disk change notification polling detects the media change, causing autorun to trigger on the media. The operating system (Windows, Linux, etc) checks in the new disk's root directory for the existence of autorun.inf. If absent, the operating system performs a default action such as the auto insert notification action selection dialog in XP.
Simple autorun.inf example: [autorun]
open=autorun.exe icon=autorun.ico
See Creating an Autorun.inf for more information.
Linux Specific
In Linux autorun automagically recognises all available CDROMs in your system, mounts them upon insertion and executes a possible 'autorun' executable on the CD. To allow an ordinary user to do this you have to add the options user,exec in /etc/fstab to the CDROMs you want to use.
There is also Autorun.desktop for KDE.
References and Sources
- Computer Hope Enabling or disabling Windows AutoPlay
- Computer Helper How to Turn Off AutoRun, Auto insert, and AutoPlay
- Moon Valley Software Autorun.inf, What is it?
Related
- Autoplay, Autorun, and Auto-insert notification
- Turn off Autoplay With Group Policy Editor
- Sandisk U3 Flash Drive Virus
- Sony DRM Rootkit
For Linux Users:
Key Words: spyware , malware , trojan , crash , aries.sys , XCP technology